
Have you ever heard of SSH, and you wonder what is SSH and what does it stand for? We have come up with everything you need to know about this term. SSH is basically called Secure Shell. It is a secure or cryptographic network convention. This protocol enables the secured communication network over an insecure one. The basic purpose of SSH development is the replacement of all old insecure protocols and improve the security and privacy across all operating systems out there. We have come up with an answer to the question, What Is SSH? All you need to know!
What Is SSH?
As we’ve mentioned earlier, SSH stands for Secure Shell. It is also known by the name of Secure Socket Shell. This is a secured network convention. The network administrators use this communication protocol in order to connect to the remote devices securely and safely. When SSH was not present in the market, the insecure network protocols were used by administrators and various users. These insecure protocols include Telnet, which was mainly used to communicate with devices located far away. Those old protocols used to send critical information, including password and login information. Because of a lack of security and privacy, this kind of protocol was more likely to get attacked by hackers. Port 22 is a typical communication port of SSH.
SSH1 Vs. SSH2
SSH comes in two forms or versions. These versions are considered separately because many implementations and updates have resulted in the formation or development of SSH 2 from SSH 1. At this point, you must have guessed that SSH 2 is more secure and safe as compared to SSH 1. The protection provided by SSH2 is more reliable in comparison with SSH 1. Your system will be protected against all kinds of hackers, attackers, and eavesdroppers if you use SSH 2. Similarly, the support provided by SSH 2 against encryption algorithms makes it better than the original SSH protocol.
What Is OpenSSH?
The open-source implementation of SSH that is used widely is called OpenSSH. Tatu Ylonen was the developer of the actual or original version of SSH. The versions that were released later by Ylonen were paid. They did not allow the users to access them anytime. Moreover, no unauthorized changes were allowed with them. That is when the original version of SSH, which was free of the cast, was separated. The developers gave it the name of OpenSSH. The best thing about OpenSSH is that all the major operating systems support it; whether it be macOS, Windows, or Linux, every OS supports this free SSH.
How Does SSH Work?
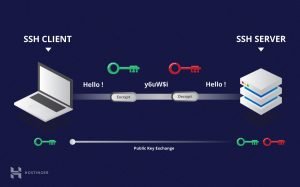
The understating of two things is a must before getting into the understanding of SSH. The first thing that you need to know is what a shell is? The second important thing in the working of SSH is the working of public-key cryptography. So, we have come up with an introduction to shell and how does public-key cryptography work. So, let’s get into their introduction first.
What Is a Shell?
A shell is actually a fragment of software. It allows the user to communicate with the OS it is hosted on. The commands are often used to interact with the shell, but the Graphic User Interfaces (GUIs) exist in the market for interaction with the shell. One amazing thing that deserves mention here is that the user is not required to sit in front of his PC in order to interact with the shell. The shell can be operated remotely too. This required a network connection, which is none other than SSH.
What do you mean by Public-Key Encryption?
When we talk about modern computing, two types of primary encryption are generally considered. These are:
Symmetric algorithm
The symmetric algorithm, as the name suggests, is symmetric. This means that it uses the same key for encryption as well as decryption. The compulsion that accompanies the symmetric algorithm is both parties’ agreement on the algorithm key before initiating the communication.
Asymmetric algorithm
The asymmetric algorithm uses two different keys, unlike the symmetric algorithm. First is the pubic and second is the private key. This allows secure encryption during communication and doesn’t require any previous mutual algorithm.
SSH uses both symmetric and asymmetric algorithms and is a type of public-key cryptography. Both these algorithms are used by it in the establishment of a secure connection. The connection is made in a client-server model. Each party communicates the encryption protocol once the clients initiate a connection with the server.
The client and the server use the Diffie-Hellman Key Exchange Algorithm after coming to a matching encryption protocol. The encryption is not revealed and is later used to encrypt the entire communication between both parties.
What Encryption Algorithm is used by SSH?
As we have mentioned earlier that symmetric encryption is used by SSH for the establishment of a secure connection. The symmetric encryption algorithms used by SSH include AES, Twofish, 3DES, IDEA, Salsa20/ChaCha20, and much more.
Is SSH the same as SSL/TLS?

Both of these work in making a previously insecure network secure, but they are not the same.
The Secure Sockets Layer (SSL) and its successor, Transport Layer Security (TLS), work in providing a communication tunnel. The tunnel they provide is actually encrypted. TLS is used in the daily routine life in sending emails and browsing the web. Both SSL and TSL are basically application layer protocols.
Instead of doing the same task at the end of the day, which is the encryption of communication network protocols, the design of both SSH and SSL/TSL is entirely different. In simple words, the data connection is protected and secured through SSL/TSL. SSH works in providing secure and safe remote access.
Instead of the difference between the two protocols, SSH can be used in coordination with SSL. This conjunction is used to transfer files.
What are the Platforms on which SSH is available?
If the operating system you have chosen for yourself has an SSH client in it or has integrated SSH functionality, you can access the secure network protocol.
SSH Is Here to Shine!
SSH or Secure Shell is not momentary. It is meant to shine and will stay here. The easy-to-use network provided by SSH is easily available for the users. Moreover, the versatility and global acceptance of SSH deserve mention. This guide on “What Is SSH? All you need to know!” will help you out in the future when you have to use this.




![Photo of How to Enable Edge Flags [5 Best Flags]](https://techstuff.website/wp-content/uploads/cover-1024x576-1-390x220.png)